OSEE Exam Review — My Preparation, Experience, and Insights

1. Introduction
On July 13, 2024, I successfully passed the “OffSec Exploitation Expert (OSEE)” certification exam. The OSEE certification is currently regarded as the most challenging among OffSec’s Exploit Development — focused qualifications.
What this article covers:
- An overview of the OSEE exam
- How I prepared for the exam
- My experience on exam day
- Impressions after the exam
Who this post is for:
- Those considering taking the OSEE
- Anyone curious about what the OSEE exam is like
This article is a follow-up to a previous post I wrote in May. If you would like to learn more about the specific topics covered in the Advanced Windows Exploitation (AWE) course, please refer to my earlier write-up.
Table of Contents
- 1. Introduction
- 2. OSEE Exam Structure
- 3. My Exam Preparation
- 4. My Exam Experience
- 5. Post-Exam Reflections
- 6. Conclusion
2. OSEE Exam Structure
Among OffSec’s certifications, the OSEE exam is somewhat unique. Below, I will discuss its format and what sets the problems apart.
2.1. Exam Overview
As stated on the official page, the OSEE exam format is as follows:
- Duration: 71 hours and 45 minutes
- Report submission deadline: Within 24 hours after the exam ends
- Number of challenges: 2
- Scoring: Each challenge is worth 50 points (partial credit of 25 points available under specific conditions)
- Passing score: 75 points
Notably, OSEE comes with the longest exam period among OffSec certifications — nearly four days if you include time to write the report. This length alone makes it stand out significantly as a certification test.
Another key feature is that you must attend an in-person, live training session (EXP-401: AWE) to be eligible. Most other OffSec certifications can be pursued through online training alone, but OSEE requires in-person participation (though the exam itself is held online).
2.2. Characteristics of the Challenges
There are only two problems in total. Spending roughly 72 hours on just two tasks may seem difficult to picture, but a good analogy is “writing two modern exploit codes within three days” — for example, a VMware guest-to-host escape or a browser sandbox escape. This gives a clearer sense of the complexity involved.
Below are a couple of exploit code repositories I created while preparing for the OSEE exam. The exploit development process you’ll face during OSEE is similar to what you see in these examples:
- GitHub — ommadawn46/chakra-type-confusions: Chakra Type Confusions — PoCs of Edge’s legacy JS engine vulnerabilities that inject code into the JIT process
- GitHub — ommadawn46/HEVD-BufferOverflowNonPagedPoolNx-Win10–22H2: HEVD Exploit: BufferOverflowNonPagedPoolNx on Windows 10 22H2 — Escalating from Low Integrity to SYSTEM via Aligned Chunk Confusion
2.3. Official Information
For more detailed information about the exam format, refer to the EXP-401: Advanced Windows Exploitation OSEE Exam Guide. If you want to know more, this resource is invaluable.
3. My Exam Preparation
From finishing my previous article to the actual exam date, I’ll recap what I did during that time. I had roughly two months in total for focused exam prep.
3.1. Kicking Off My Prep
I originally took the AWE course in February. Around that time, my role at work changed, and I suddenly had a mountain of other things I needed to study. As a result, I didn’t touch any OSEE prep for a few months. Eventually, things settled down, and I was able to start serious OSEE prep around May, when I wrote my previous post.
Once I finally committed to diving into exam prep, the first thing I did — even before I started studying — was schedule my exam. I wanted to create a hard deadline that would force me to hustle. (To be honest, I know myself well enough to recognize I won’t get moving without a fixed deadline looming over me.) I booked my exam for July and decided to cram all my prep into the remaining time.
In the following sections, I’ll explain in more detail how I tackled my exam preparation during those two months.
3.2. Revisiting the AWE Course
As mentioned in my previous article, the AWE course primarily consists of four main modules:
- VMware Workstation Guest-To-Host Escape: Exploiting VMware Workstation vulnerabilities to escape from guest OS to host OS
- Microsoft Edge Type Confusion: Exploiting Microsoft Edge vulnerabilities to escape the Browser Sandbox
- Driver Callback Overwrite: Exploiting vulnerabilities in third-party kernel drivers for local privilege escalation
- Unsanitized User-mode Callback: Exploiting vulnerabilities in Windows OS native kernel subsystems for local privilege escalation
These modules can be broadly categorized into User-mode Exploits (VMWare, Edge) and Kernel Exploits (Driver, Windows Kernel).
3.3. Learning from the Course Material
Looking back at the immediate aftermath of completing the AWE course in February, I admit I was somewhat overconfident, thinking, “Exam preparation shouldn’t take too long.” As mentioned in my previous article, earning two challenge coins during the course probably contributed to this excessive confidence. However, when I revisited the exploit code in the course material in May, I realized there were many areas where my understanding was vague.
3.3.1. The Gap Between Course and Exam
The course challenges generally involve modifying existing exploit code to achieve specific goals. However, this is entirely different from writing exploit code from scratch. The exam requires you to complete exploit code from the ground up, so succeeding in the course challenges doesn’t necessarily mean you’re prepared for the exam. It became clear that I needed to focus on learning how to write exploit code independently.
3.3.2. Specific Study Approach
Recognizing this situation, I decided to approach my studies using the AWE course textbook, following this process for each module:
- Thoroughly read the exploit code in the textbook, repeatedly debugging to eliminate any areas of vague understanding
- Rewrite the exploit code from scratch by myself
- Solve all the previously unattempted Extra Mile problems
It took about a month and a half to cover all modules following this approach.
The process went smoothly overall, but one particular Extra Mile problem was exceptionally challenging, taking over a week to solve. Interestingly, I found this to be the most enjoyable part of my preparation.
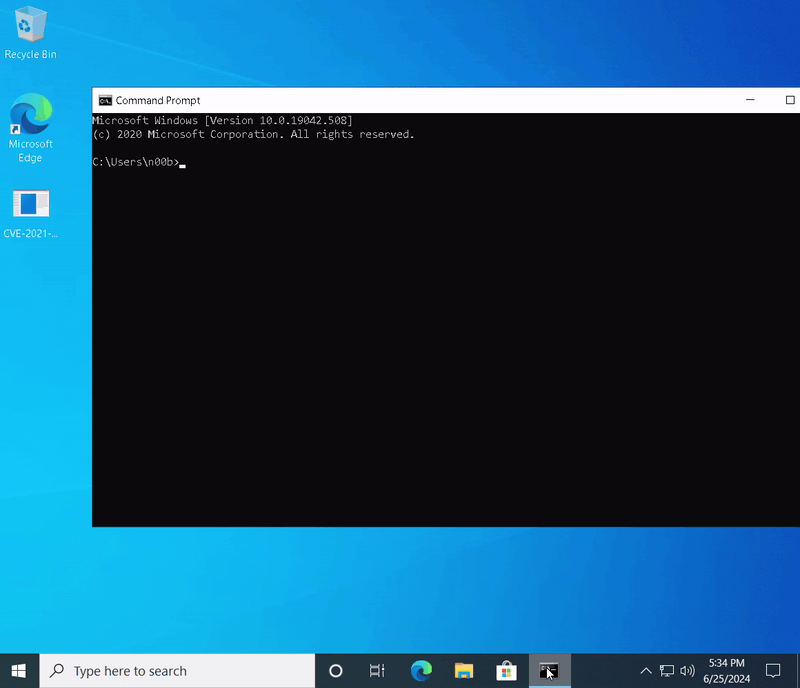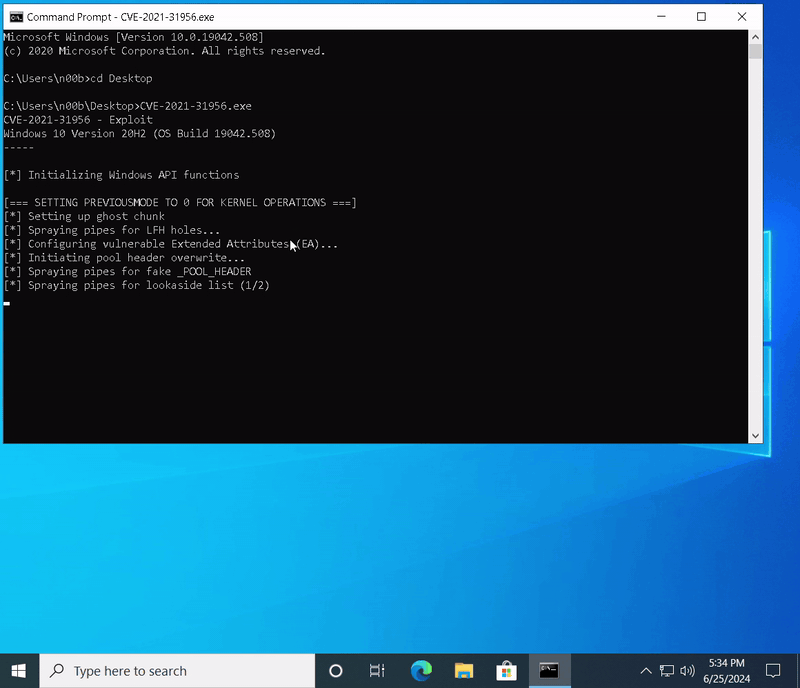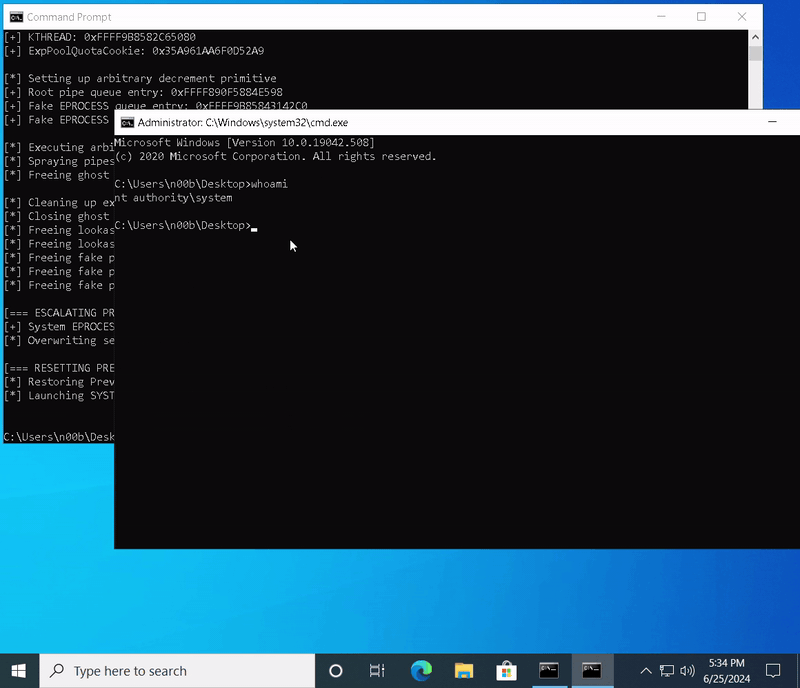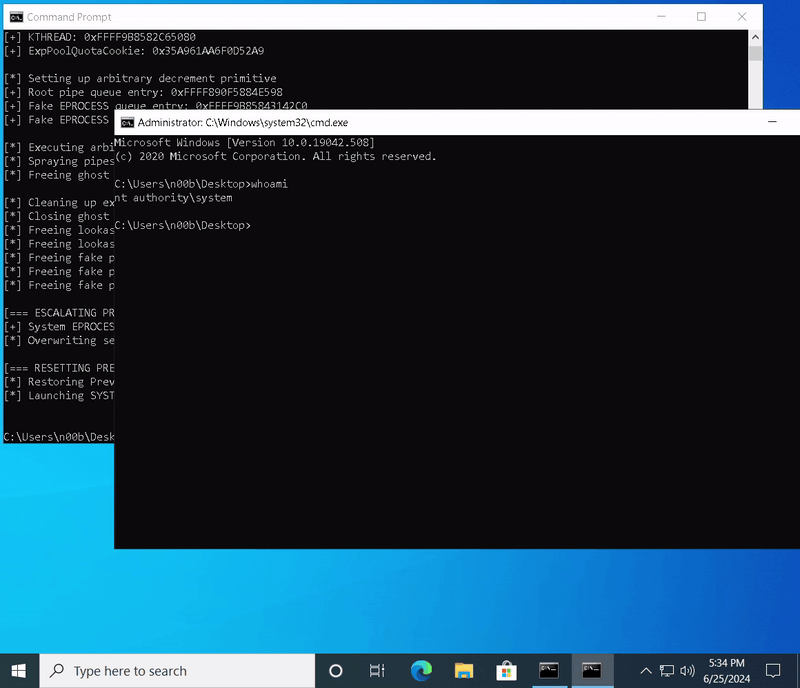
While there were quite a few untouched problems in the Exercises section apart from the Extra Miles, I decided to focus more on Kernel Exploit preparation, which I’ll discuss later, and concluded my textbook-based learning at this point.
3.4. Additional Learning
3.4.1. Kernel Exploit Preparation
For the remaining two weeks before the exam, I concentrated on Kernel Exploit preparation. Specifically, I delved deeper into the techniques related to the most challenging Extra Mile problem mentioned earlier.
I later published the exploit code I developed during this learning process on GitHub:
Writing exploit code independently seems to be the most effective exam preparation method. I felt my skills improved the most during the period when I was writing the above exploit code while reverse engineering the Windows kernel.
3.4.2. User-mode Exploit Preparation
In addition to the Kernel Exploit learning, I had intended to study User-mode Exploits (such as Chrome vulnerabilities for sandbox bypasses) as well. However, I miscalculated my time allocation and ran short on study time.
As a result, my exam preparation ended up heavily skewed towards Kernel Exploits. This lack of User-mode Exploit preparation would later prove challenging.
While my study was imbalanced, I recommend that future exam takers allocate equal time to both User-mode and Kernel Exploit preparation. Ideally, you should spend roughly the same amount of time on each.
3.4.3. Additional Reference Materials
The OSEE exam differs from other OffSec exams in several ways. I highly recommend carefully reading the official guide from cover to cover before taking the exam.
- EXP-401: Advanced Windows Exploitation OSEE Exam Guide — OffSec Support Portal (mentioned earlier)
I found the sample report particularly helpful to review in advance. You can glean a lot of information from the sample report, helping you form a clearer picture of what to expect in the exam.
Additionally, reading experience reports from those who have taken the OSEE exam can help you better understand what to anticipate.
- OSEE, an Unexpected Journey | Blog | Fluid Attacks
- Advanced Windows Exploitation (OSEE) Course Review: Part 2
- OffSec EXP-401 Advanced Windows Exploitation (AWE) — Course Review — VoidSec
- OSEE Review 2023
- Passing the New OSEE Exam After Forgetting Everything | Spaceraccoon’s Blog
4. My Exam Experience
This section details my thoughts and experiences during the actual exam. Note that I won’t discuss the content of the exam questions, focusing instead on my personal reflections.
To summarize my overall exam experience in one word: “Exhilarating!” While I’ve enjoyed all of OffSec’s exams, OSEE was particularly thrilling.
4.1. Pre-Exam
My exam was scheduled as follows:
- Start time: July 13, 12:00
- End time: July 16, 11:45
- Report submission deadline: July 17, 11:45
On the day of the exam, I logged into the Proctoring Tool 15 minutes before the start time. The passport ID check and room check went smoothly. Just as I thought the exam was about to begin, the proctor’s responses became delayed, causing some anxiety. Then, I received a message stating there was a technical issue on the server side and I should wait.
All I could do was wait, which was somewhat uncomfortable as I was under camera and screen-sharing surveillance.
The exam finally started after 1:00 PM. By this time, I was already feeling a bit tired, which felt like an inauspicious start.
4.2. During the Exam
Immediately after the exam began, I spent about an hour researching both questions. While both seemed challenging, I felt one of the two was particularly difficult.
After some deliberation on where to start, I decided to tackle the more difficult problem first. My reasoning was that, given the grueling three-day marathon ahead, it would be better to address the most challenging task while my performance was at its peak.
4.2.1. The First Challenge
As expected, this problem proved highly challenging and I struggled significantly.
Here’s a timeline of my progress on this problem:
- July 13, 14:00: Started working on the problem
- July 14, 04:40: Achieved partial credit (25 points)
- July 14, 04:50: Went to sleep
- July 14, 10:10: Woke up
- July 14, 23:40: Achieved full credit (50 points)
It took about 34 hours to complete this challenge. Looking back, I felt like I was groping in the dark the entire time. Every bit of progress led to another obstacle, and this cycle repeated itself. Until the very moment I solved it completely, I questioned whether this problem was actually solvable as designed.
On the first day, I continued this fumbling process until dawn, making slow but steady progress until I secured partial credit. I went to bed immediately after, but honestly, I couldn’t rest well. I remember having unsettling dreams and only getting light sleep.
After waking up, progress remained slow. There were times when I made no headway at all, and I was constantly haunted by the fear that I might not solve the first question before the exam ended. Eventually, I found a breakthrough and finally solved the problem in the early hours of the second day.
This was the happiest moment of the exam for me. However, my joy was quickly tempered by a new worry: “If the second question takes even longer than this, passing might be out of reach…”
To be honest, I had no peace of mind during the first and second days.
4.2.2. The Second Challenge
I approached this challenge with apprehension, but surprisingly, I was able to solve it relatively quickly.
Here’s the timeline for the second challenge:
- July 15, 00:00: Started
- July 15, 04:30: Achieved partial credit (25 points)
- July 15, 04:40: Went to sleep
- July 15, 11:40: Woke up
- July 15, 16:50: Achieved full credit (50 points)
It took about 17 hours to complete this challenge. In stark contrast to the first problem, this one progressed smoothly, feeling like I just needed to execute what I thought was necessary. I worked until dawn to achieve partial credit, comfortably reaching the passing score.
Afterwards, I was able to go to bed with a sense of relief and slept better than the previous night.
After waking up, I encountered no significant hurdles and successfully completed the second challenge.
With this, I had solved both problems. Given that I started the exam around 13:00 on July 13, it took approximately 52 hours to complete both challenges.
4.2.3. Report Writing
After taking ample breaks, I proceeded to refactor the exploit code and gather materials (such as screenshots) for the report.
Here’s the timeline for report creation:
- July 15, 17:00: Started refactoring & gathering report materials
- July 16, 00:20: Began writing the report
- July 16, 07:20: Submitted the report
I spent about 7 hours on report creation. Initially, I had planned to sleep before finishing the report, but once I started writing, I got into a flow state and ended up working through the night until morning.
4.3. Result Notification
I submitted my report at 07:20 on July 16, concluding my OSEE exam.
Then began the anxious wait for the results.
I found myself jumping at my phone every time I received an email, but the results didn’t arrive. As time passed, I started to worry that there might have been some issue with my submission, and my anxiety gradually increased.
After two weeks had passed since submission, I couldn’t wait any longer and inquired about the exam grading status with OffSec. They explained that the AWE course was being held at Black Hat USA 2024 from August 3–6, and preparation for this event had delayed the grading process.
I suspect that only AWE course instructors can grade the OSEE exam, making it difficult to grade exams while preparing for Black Hat. Given the advanced nature of the course and the complexity of grading, this is understandable. In retrospect, my timing for taking the exam wasn’t ideal.
Finally, on August 8, three weeks after submitting my report, I received the pass notification.

I did it!
5. Post-Exam Reflections
In this section, I’ll reflect on my experience from AWE course attendance to OSEE certification, now with the perspective of having passed the exam. I’ll mainly share my thoughts on the exam content and its real-world benefits.
5.1. Exam Challenge Design
Here are my thoughts on the OSEE exam challenges.
While solving the problems, I felt that the knowledge and skills I had acquired during my exam preparation were being fully utilized, giving me a sense that my abilities were being thoroughly tested. As a certification exam, I found it to be a satisfying experience.
The challenge design seemed to include twists that tested not just the techniques learned in AWE, but also our ability to apply that knowledge. It gave me the feeling of “This is what an OffSec exam should be like.”
5.2. Application to Modern Environments
I believe that the technologies and concepts covered in OSEE are still highly relevant in today’s environments.
Kernel Exploits in VBS/HVCI-enabled environments, and User-mode Exploits in applications with multi-layered sandboxing like VMs and browsers — these Exploit Development techniques are at the forefront of the field in 2024. The skills learned in the course and exam seem to be directly applicable to real-world scenarios in 2024.
5.3. Application to Other Environments
5.3.1. OSEE is Windows x86_64 Specific
The Exploit Development techniques learned in OSEE are specifically tailored for the Windows x86_64 architecture. As such, they are directly applicable only to Windows x64 environments. Moreover, many of the techniques learned in OSEE are directly applicable only to exploits for specific software.
5.3.2. Non-Generic Exploit Techniques
OSED focuses on generic exploit techniques like ROP for DEP bypass.
In contrast, OSEE emphasizes exploitation methods that heavily depend on the unique behavior of specific software:
- Understanding the meaning of each data element in structures
- Comprehending how modifications affect software behavior
- Considering how to bypass specific security features or sandbox mechanisms to construct primitives
- Expanding available primitives and exploring ways to ultimately achieve the goal
The methods for constructing primitives and achieving objectives vary greatly depending on the software. Techniques that succeed for one target are unlikely to be directly applicable to another.
5.3.3. Generic “Analytical Skills”
However, while direct application might be limited, I believe that the “analytical skills” developed through OSEE can be applied to other software and environments. In OSEE, we learn to understand software internals, analyze data structures, and consider how to manipulate data to maximize exploit impact. I think these analytical skills, developed through the Exploit Development process, can be abstracted and applied not just to Exploit Development, but even to exploiting web vulnerabilities.
In my opinion, whether it’s Web or Binary, what’s crucial in exploitation is thinking through how to maximize the abuse of unintended behaviors, and the key to this is how deeply we can understand the internal workings of the software. Among OffSec’s courses and certifications, I feel that OSEE pushes us to consider this point more deeply than any other.
In terms of developing these crucial analytical skills for exploitation, I believe OSEE offers the most significant learning experience. Of course, knowledge specific to new environments will require additional study. However, I believe the thought processes cultivated through OSEE can be a powerful tool in any software or environment.
5.4. Real-World Applications
5.4.1. Offensive Security Operations in General
As mentioned earlier, I believe the analytical skills developed through OSEE are valuable across all offensive security operations. This is where I personally feel the greatest benefit.
5.4.2. Penetration Testing
More specifically, the Exploit Development techniques learned in OSEE could serve as a “secret weapon” in penetration testing scenarios. In penetration tests, we occasionally encounter situations where the scope is so narrow that we run out of things to do midway. While normal operations typically involve discovering known vulnerabilities or misconfigurations, the skills acquired through OSEE could potentially allow us to discover and exploit zero-day vulnerabilities in seemingly secure software, enabling us to achieve our goals. In this way, OSEE skills might serve as a final resort when all other options have been exhausted. (Although, realistically, such opportunities might be rare.)
5.4.3. Analysis of Complex Vulnerabilities
For those in roles involving the analysis of complex vulnerabilities, there may be many opportunities to apply what we’ve learned. For instance, when vulnerabilities like the recent CVE-2024–38063 are disclosed, the skills required to diff Windows OS binaries, analyze the vulnerability, and assess its exploitability are precisely those demanded by the OSEE exam. The role of capturing vulnerability risks through such analysis might be where OSEE skills can be most clearly utilized.
6. Conclusion
6.1. What OSEE Means to Me
The sense of achievement I felt upon receiving the OSEE pass notification was immense, and I’m still filled with joy.
However, it’s rare to find something that allows you to lose track of time and become so deeply absorbed. While I’m happy, I also feel a slight sadness at having lost that. When I recall the days of analyzing binaries, writing exploit code, and battling bugs into the night, I feel a bit nostalgic.
For the past few years, obtaining the OSEE certification has been my goal. I remember how excited I was when I finally got the opportunity to participate in the AWE course after eyeing it for so long. Subsequently, through the course and exam, I was able to immerse myself deeply in technology again, experiencing truly enjoyable days.
6.2. How I’ll Use My OSEE Skills
To be honest, in my case, I’m gradually moving away from frontline security operations and vulnerability analysis that directly utilize these skills. Rather than relying solely on my individual capabilities, my current focus is more on management and strategy formulation, requiring a more holistic perspective to ensure that those around me can maximize their technical prowess.
Amidst various non-technical tasks, OSEE provided me with a technical challenge and valuable time to gain new perspectives. I believe the knowledge and skills cultivated through OSEE, especially the ability to understand software internals, will certainly be beneficial in my current role.
In any case, obtaining the OSEE certification has become a significant source of confidence for me.
6.3. Acknowledgments
Lastly, I’d like to express my gratitude to OffSec for providing this fantastic challenge, and to the instructors, Morten and Sickness.
I’m also grateful to all of you who have read this far. I hope this article provided some useful insights.
Until next time!
This article is an English translation of https://ommadawn46.hatenablog.com/entry/2024/08/29/200907.
