EXP-401: Advanced Windows Exploitation (AWE) — My Preparation and Experience

Introduction
In February 2024, I participated in OffSec’s EXP-401: Advanced Windows Exploitation (AWE) course held in London.
The AWE course is renowned as the most advanced offering in OffSec’s lineup, being the only course assigned a 400-level course number (as shown in the bottom right of the image below).
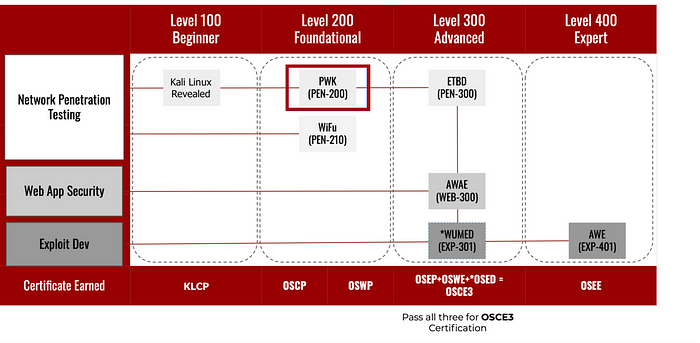
This training is paired with the notoriously challenging OSEE exam and stands out as the sole course in OffSec’s portfolio that is exclusively conducted as a live, in-person training.
In this article, I’ll be sharing the following information about the AWE course:
- The themes and content covered in the AWE course
- The preparations I made before attending the course
- My experience participating in the AWE course
Please note that as of May 2024, I have not yet taken the OSEE exam. This article focuses solely on the AWE course, which serves as the foundation for the OSEE certification.
(Update) I have passed the OSEE exam: OSEE Exam Review — My Preparation, Experience, and Insights
Table of Contents
- Introduction
- 1. Course Overview
- 2. Course Content
- 3. How to Participate in the Course
- 4. My Preparation
- 5. My Experience in London
- 6. Conclusion
1. Course Overview
What is EXP-401: Advanced Windows Exploitation (AWE)?
EXP-401: Advanced Windows Exploitation (AWE) is a course dedicated to advanced exploit development in Windows environments.
Structure of the AWE Course
This course follows a recurring process along these lines:
- You are provided with proof-of-concept (PoC) code for a well-known piece of software (the code reproduces the bug but doesn’t fully exploit it).
- Using the PoC code as a starting point, you reverse engineer the target software to uncover the details of the vulnerability.
- You investigate how the vulnerability can be exploited and then develop exploit code that achieves the intended goal, such as arbitrary code execution or privilege escalation.
A key feature of this course lies in its intensive focus on “thoroughly analyzing known bugs to verify and implement exploitability.”
By repeatedly going through the process of “taking the provided PoC code, performing in-depth analysis on the vulnerability, and creating a working exploit from scratch,” you acquire the skills to develop exploit code on your own.
Real-World Application
In real-world scenarios, we often encounter situations where PoC code that causes crashes, such as those related to memory corruption bugs, is publicly available. However, it’s often unclear whether these bugs are actually exploitable.
A common example is when platforms like Google Project Zero publish PoC code that only demonstrates a crash, without confirming exploitability.
The AWE course simulates this scenario by repeatedly going through the process of starting with such PoC code, verifying exploitability through reverse engineering, and ultimately developing zero-day exploit code.
Each module covers various targets (VMs, browsers, drivers, OS), and the course is designed to help students acquire exploit development techniques using vulnerabilities that have been assigned actual CVE numbers as subjects.
About OffSec Exploitation Expert (OSEE)
Completing the AWE course makes you eligible to take the OffSec Exploitation Expert (OSEE) exam. As of 2024, OSEE is considered “the most difficult exploit development certification you can earn” and is recognized as the most challenging certification in the offensive security field.
OSEE is positioned at the top of the Security Certification Roadmap (see the figure below).

Now that we’ve gone over the AWE course overview, let’s dive deeper into the course content.
2. Course Content
In this section, I will explain the evolution and current content of the AWE course.
Relationship with the Lower-Level Course (OSED / EXP-301)
Within OffSec’s certification lineup, OSED / EXP-301, which is also classified under Exploit Dev, is positioned as a lower-level course to OSEE / EXP-401. Comparing the two, there are the following differences, creating a complementary relationship:
1. OSED / EXP-301:
Objective:
・Master fundamental exploit development concepts
Content:
・Basic vulnerabilities in Windows user mode (stack overflows, SEH overflows, etc.)
・Bypassing basic mitigations (DEP, ASLR)
・Use of fundamental tools (WinDbg, IDA Pro)
2. OSEE / EXP-401:
Objective:
・Acquire modern exploit development techniques applicable to real-world scenarios
Content:
・More complex attack scenarios (escaping virtualized environments, browser exploits, kernel exploits)
・Bypassing cutting-edge mitigations (CFG, ACG, VBS, etc.)
・Advanced exploit techniques (heap exploitation, out-of-context calls, etc.)
Syllabus
Evolution of the AWE Course
The AWE course content has been revised several times to remain current.
During a significant content refresh conducted by OffSec around 2021, some content from the old OSCE and OSEE was moved to the current OSED, and OSEE was made more advanced.
Here’s an overview of the evolution of the AWE course based on past syllabi recorded in the Internet Archive:
1. 2009
- The 2009 version covered only user-mode exploits, including Egghunter techniques and DEP bypasses, which are now part of OSED.
2. 2011
- Some topics such as Egghunter techniques were redistributed to OSCE.
- In the 2011 version, new topics like Kernel Driver exploits were added.
3. 2015
- The 2015 version included topics on bypassing multi-layered defenses like the Exploit Mitigation Experience Toolkit (EMET).
4. 2018
- The 2018 version added topics like Microsoft Edge browser sandbox escape.
Overall, OSEE has evolved from user mode to kernel mode and from simple exploits to bypassing multi-layered defenses like sandbox escapes.
5. 2021 (Latest)
- With the introduction of OSED in 2021, DEP/ASLR bypasses were moved to OSED.
- The 2021 version (latest version) added a new topic: Kernel Subsystem (win32k) exploits.
Generally, OSEE has kept its advanced status by shifting commonplace exploit development techniques to lower-level courses and adding new topics through periodic revisions.
The current OSEE has reached its highest level ever in terms of both volume and difficulty.
Latest Version
As of May 2024, the 2021 version is the latest AWE course content. The course is divided into five main modules, each covering the following topics:
1. Custom Shellcode Creation:
・Creating custom shellcode from scratch for the x64 architecture
2. VMware Workstation Guest-To-Host Escape:
・Escaping from the guest OS to the host OS by exploiting vulnerabilities in VMware Workstation
3. Microsoft Edge Type Confusion:
・Escaping from the browser sandbox by exploiting vulnerabilities in Microsoft Edge
4. Driver Callback Overwrite:
・Local privilege escalation by exploiting vulnerabilities in third-party kernel drivers
5. Unsanitized User-mode Callback:
・Local privilege escalation by exploiting vulnerabilities in the native Windows OS kernel subsystem
For more details, check the AWE course syllabus.
That wraps up our look at the AWE course content. Next, I’ll walk you through the application process for joining the course.
3. How to Participate in the Course
In this section, I will explain the application process for the AWE course and the differences between events.
Applying for Participation
Upcoming Events
You can view a list of upcoming live courses on OffSec’s official Upcoming Live Training & Events page. Events marked as “EXP-401 Live Training” are AWE events, and as of the time of writing this article, five more events are scheduled for the remainder of 2024.
You can register for the AWE course by applying through these event pages.
Competition for Seats
The AWE course is known for its high demand. In the past, at Black Hat USA, the seats were filled up within minutes of the start of registration.
Past participants recommend setting up a system to monitor the release of the training page and receive immediate notifications upon its release. This suggests that securing a seat is the most challenging aspect of the AWE course.
However, this is a thing of the past, and it seems that the competition has decreased recently, perhaps due to the increase in participation fees and the number of times the training is held. Currently, securing a seat is not difficult if you have the budget.
Differences by Event
Since the AWE course is a live course, there are several differences depending on the event you participate in.
Course Schedule
At Black Hat USA, the course is offered over four days, while at other events, it is typically provided over five days.
I participated in the five-day course offered by QA in the UK.
The five-day schedule was set up with lectures held daily from 9:00 a.m. to 5:00 p.m., with time for direct Q&A with the instructors before and after the lectures.
Course Instructors
In recent years, the AWE course has been taught by Morten & Sickness.
However, it seems that the lineup of instructors for the AWE course has been expanded starting this year. For example, at BlackHat USA 2024, a company called Applied Technology Academy is providing course instructors, suggesting that the course will be conducted in a different structure than before.
The intense competition for seats mentioned earlier was rumored to be due to the limited number of times the course could be held because of the busy schedules of the two instructors. While the expansion of the instructor lineup leading to an increase in the number of course offerings and a lowering of the barrier to participation in the AWE course is desirable, it should be noted that most of the AWE reviews currently available, including this article, are based on events where Morten & Sickness were the instructors.
It will be interesting to see how this change in structure will affect the course experience.
Specs of the Machine I Brought
I brought a machine with the following specs to the course:
- OS: Windows 11 22H2
- CPU: 11th Gen Intel® Core™ i7–1165G7 Processor
- RAM: 16GB
However, with the above machine, the performance became so slow that it was difficult to debug properly during the VMware exercises on the second day.
I haven’t verified whether the CPU performance is the bottleneck or if increasing the RAM would solve the issue, but it might be safer to prepare a machine with higher specifications.
Having explained the application process, I’d now like to describe the preparation I did for these topics.
4. My Preparation
In this section, I will explain the resources that helped me prepare and the specific preparation methods I practiced.
Preparation Approach
The AWE course is conducted entirely in English, and to be honest, I am not particularly skilled in English. I anticipated that I would be able to understand, at best, only about half of the lectures through listening.
Therefore, to compensate for the language handicap on the day of the course, I decided to thoroughly prepare before heading to London.
The following are the approaches I took when preparing for the AWE course:
1. Keyword Extraction:
List unfamiliar keywords from the AWE course syllabus.
・e.g., SMEP, PML4 Self-Reference Entry
2. Reading Technical Articles:
Search for technical articles related to the keywords, read them, and deepen understanding.
・e.g., Analysis of a VMWare Guest-to-Host Escape from Pwn2Own 2017 | Linxz’ Blog, Exploit Development: Browser Exploitation on Windows — CVE-2019–0567
3. Exploit Development:
Utilize resources that provide hands-on experience and actually write exploit code.
・e.g., ommadawn46/chakra-type-confusions, ommadawn46/HEVD-Exploit-Win10–22H2-KVAS
Module-Specific Preparation
The following is a summary of the keyword-based prior learning I conducted based on the latest version of the syllabus:
1. Custom Shellcode Creation
Judging from the syllabus, it seemed like a 64-bit version of the shellcode creation practiced in OSED, with almost equivalent concepts, so I did not do any specific preparation.
2. VMware Workstation Guest-To-Host Escape
I prepared by reading articles on past vulnerabilities in VMware Workstation. The main theme, Use-after-free (UaF), was a topic I had already experienced in CTF, so with the assumption that I had a grasp of the basic knowledge, I limited my preparation to reading materials.
Keywords:
・VMware
・Guest-To-Host Escape
・UaF
Articles Read:
・Analysis of a VMWare Guest-to-Host Escape from Pwn2Own 2017 | Linxz’ Blog
・Zero Day Initiative — Use-After-Silence: Exploiting a quietly patched UAF in VMware
・A bunch of Red Pills: VMware Escapes | Keen Security Lab Blog
Exploit Developed:
・None
3. Microsoft Edge Type Confusion
I prepared by reading Connor McGarr’s blog posts, reverse engineering Edge according to the steps in the articles, and writing exploit code, with an emphasis on actually putting my hands to work.
Keywords:
・Microsoft Edge
・Type Confusion
・CFG
・ACG
Articles Read:
・Exploit Development: Browser Exploitation on Windows — CVE-2019–0567, A Microsoft Edge Type Confusion Vulnerability (Part 1) | Home
・CVE-2019–0539 to Remote Code Execution (RCE) | Perception Point
Exploit Developed:
4. Driver Callback Overwrite
I read Matteo Malvica’s blog post, and prepared with an emphasis on hands-on practice by creating an exploit targeting HEVD based on the methods introduced in the article. I have summarized the details of the preparation I conducted for this module in a blog entry.
Keywords:
・SMEP
・PML4 Self-Reference Entry
・KVA Shadow
・Token Stealing
Articles Read:
・Kernel exploitation: weaponizing CVE-2020–17382 MSI Ambient Link driver :: — uf0
・Meltdown Reloaded: Breaking Windows KASLR by Leaking KVA Shadow Mappings | Bluefrostsecurity
・Bypassing SMEP
Exploit Developed:
My Blog Entry:
5. Unsanitized User-mode Callback
I read Shawn Westfall’s blog posts. I wanted to write code and get hands-on practice for this as well, but I didn’t have enough time before the course, so my preparation was limited to studying the materials only.
Keywords:
・Win32k
・TagWND
・Virtualization-Based Security
・kCFG
Articles Read:
・Inside Win32k Exploitation: Background on Implementations of Win32k and Exploitation Methodologies
・Technical Analysis of CVE-2021–1732 — REAL security
・WINDOWS KERNEL ZERO-DAY EXPLOIT (CVE-2021–1732) IS USED BY BITTER APT IN TARGETED ATTACK
Exploit Developed:
・None
I began the above preparation about two months before attending the AWE course. I think I spent the most time preparing for “4. Driver Callback Overwrite,” which I also wrote an article about.
That concludes my preparation phase. Let’s move on to my actual experience at the AWE course.
5. My Experience in London
In this section, I will describe the experiences and learnings I gained from actually attending the AWE course.
Overall Impression
In conclusion, I had a highly satisfying learning experience overall. The content was as challenging as I had anticipated, and during the lectures, I was fully occupied just trying to grasp the big picture.
I was constantly on the brink of keeping up or falling behind, but this allowed me to stay focused and fully immersed in the lectures without losing concentration.
Exercises
Numerous exercises are given during the lectures, but I didn’t have enough time and completed fewer than I would have liked.
The course seemed designed for students to start working on each exercise and understand its objectives within the allotted time, rather than expecting them to fully complete all the exercises.
In other words, this course is designed to lay the foundation for several months of study afterward, rather than being a self-contained five-day program.
Approach to Taking the Course
In my case, to reinforce the points I couldn’t understand later, I focused on grasping the overview of each module and jotting down the parts I didn’t understand.
If you have strong language skills, you can learn even more by directly asking the instructors questions on the spot to clarify your doubts as you progress. (Unfortunately, my English wasn’t proficient enough to ask questions, so I did my best to gain as many insights as possible from other people’s questions and the instructors’ answers.)
Difficulty of Each Module
In the London course I attended, the course progressed at a pace of roughly one module per day over the five days. The difficulty curve of the entire course was not a steady upward climb, and I felt that the difficulty of each module was in the following order:
- Day 3 (Microsoft Edge Type Confusion) >= Day 5 (Unsanitized User-mode Callback) >> Day 4 (Driver Callback Overwrite) > Day 2 (VMware Workstation Guest-To-Host Escape) >> Day 1 (Custom Shellcode Creation)
For Day 3 and Day 5, which I found the most challenging, I feel that if I hadn’t prepared in advance, I might not have been able to keep up and would have been left behind.
Effect of My Preparation
To be honest, I think that if I hadn’t prepared, I would have hardly been able to keep up from Day 3 onward. Unless you are extremely well-versed in the lecture content, some level of advance preparation is essential.
I focused my preparation efforts on the content of Day 3 and Day 4, and looking back, I think this choice was not a bad one. As mentioned earlier, when reflecting on the entire course, I think Day 3 and Day 5 are the days where you are most likely to be left behind.
The content of Day 4 is closely related to that of Day 5, and in a sense, they are continuous. Therefore, preparing for Day 4 is essentially also preparing for Day 5.
Thanks to my preparation, I was able to understand the basic parts of Day 5 in advance, so I could attend the lectures with some leeway. The effect of the preparation was significant, in my opinion.
Challenge Problems and Prizes
In the AWE course, several homework problems are given at the end of each module. During the lecture period, it is optional to work on the homework. However, if you can solve the problems by the final day of the lectures, there is a CTF-like element where you can receive prizes set for each problem.
I gave my all to these problems, and as a result, I won one large sticker and two challenge coins.

Challenge coins are set as prizes for the most difficult category of problems, and in the event I attended, there seemed to be only a small number of participants who even attempted them.
To solve the problems, I significantly cut back on sleep and immersed myself in the problems until late at night every day. I attended the AWE course from morning to evening, then immediately returned to the hotel and worked on the challenge problems until late at night… I had the rare experience of having nothing but exploits on my mind, whether I was asleep or awake, for a full five days.
Without the challenge coins, I don’t think I could have been so absorbed for the entire five days. Personally, this challenge element was a great motivator for me.

By the way, the backs of the challenge coins are numbered, and the ones I obtained were the 29th and 31st coins.
That’s a wrap on my course experience. I’ll close with some final thoughts and my goals moving forward.
6. Conclusion
Looking back, the five days I spent in London were some of the most intense days of my life.
It was my first time traveling abroad alone, so it was challenging from start to finish, but looking back, I feel that it was a really enjoyable experience.
I spent most of the course period at the training venue and the hotel, but on the last day, I was able to do a little sightseeing in London before catching my flight.

My next goal is to pass the OSEE exam. Completing the AWE course is just the beginning of preparing for the exam, and self-study from here on is crucial. However, I’ve been busy with work and haven’t been able to study much for the OSEE in the three months since completing the AWE course. With the release of this article, I plan to resume my studies and aim to take and pass the exam soon.
If you have any questions, please contact me at @ommadawn46. I will answer to the extent that it does not violate OffSec’s policy.
I hope this article will be helpful for those who plan to take the AWE course in the future.
Thank you for reading.
This article is an English translation of https://ommadawn46.hatenablog.com/entry/2024/05/21/071143.
